Portfolio 3 Submission
- Details
- Category: Level 1, Portfolio 3 (Network Architecture, Team work)
- Published: Tuesday, 29 December 2020 16:52
- Hits: 898
Prep sheeet IPV4
Internet protocol
Internet protocol is a method which is used to send data from one device to another, each device has at least one IP address that uniquely identifies the user. When the data is sent from one device to another it is divided into little chunks called packets, each packet contains the IP address of the sender and the receiver of the data. Once the data is divided into packets it is the internet protocols job to ensure it gets to the correct destination, each packet can be sent on a separate route, but it is the IP’s job to ensure all packets reach the target destination.
What is IPV4 protocol?
IPV4 (internet protocol 4) is an internet addressing system that is used to designate addresses to every device that wishes to connect to the internet. Every device that connects to the internet needs a serial number (IP address), IPV4 uses 32-bit addresses in five different classes, these are class: A, B, C, D, and E. Class D is used for multicasting, class E is reserved for future use, and classes A B C have a different bit length and these classes are used for addressing network hosts.
The maximum number of addresses IPV4 can allocate is 4.3 billion, considering every device needs to be allocated an address, IPV4 is fast approaching its limit and will not be sustainable for future allocation of addresses.
What is IPV6 protocol?
IPV6 (internet protocol 6) is an upgrade from IPV4. The basics of IPV6 are like IPV4 with the main improvement in IPV6 being that the IP addresses are lengthened from 32-bit address to 128-bit addresses. IPV6 also supports auto-configuration, which helps correct any shortcomings experienced when using IPV4. An example of this would be IPV4 does not allow credentials used to be forwarded to another host, IPV6 makes this possible and severs can use another sever to access another sever on behalf of the original sever.
Pros using IPV4
- Reliable security
When communication with other users it is important to encrypt the data, you are sending. There are now reliable security measures for IPV4 address packets that allows data to be encrypted.
- Large routing tasks
IPV4 network allocation is vital, it becomes easy to connect to multiple devices across a large network.
- Video libraries and conferences
Because of the large number of internet users, data transfer online has become slow. IPV4 provides efficient data transfer and therefore provides a quality service for users.
- Flexible
Using IPV4 routing has become more scalable, this works well for large networks allowing data communication across networks to become more specific.
Cons using IPV4
While IPV4 is reliable and still widely used throughout the online world IP addresses are running out and is not sustainable in the long term.
- Internet use is expanding from browsing and searching data to users wishing to send more data in the form of video calls, video conferences, and online video libraries. IPV4 has limited functionality and over time has been adapted to facilitate the user’s needs.
Pros using IPV6
- Much larger address space
- Virtually unlimited host addresses
- Stateless auto configuration
- Automatic link local addressing
- Easy to type prefix lengths
- EUI 64 addressing
Cons using IPV6
- Privacy concerns
- Throttling bandwidth and banning users
- Tracking an individual personally
- Giving information to big business for lawsuits
- Giving information to the police for criminal actions
- Giving information to the government
- Using someone else’s connection to get them sued or arrested
- Difficulty with topology drawings
With all the extra space IPV6 provides it’s going to be a lot harder to fit prefixes on all of the topology drawings.
- System issues
Due to the length of the IP address IPV6 provides, in cases where you need to enter the IP address manually it may become troublesome for large networks or organisations.
Changing from IPV4 to IPV6
Due to IPV4 running out of IP addresses, it is important that there is a plan in place so large networks are prepared to start using IPV6. Governments around the world already have plans in motion to ensure the change is already happening. An example of this is the U.S Office of Management and Budget they set a deadline for their employees that had the capability to access the internet via IPV6 by 30th September 2014. Following this all vendors wishing to do business with federal government are required by the Federal Acquisition Regulation to be in full compliance with IPV6.
Research for the pros and cons of IPV6 and IPV4
Internet protocol
Internet protocol is a method which is used to send data from one device to another, each device has at least one IP address that uniquely identifies the user. When the data is sent from one device to another it is divided into little chunks called packets, each packet contains the IP address of the sender and the receiver of the data. Once the data is divided into packets it is the internet protocols job to ensure it gets to the correct destination, each packet can be sent on a separate route, but it is the IP’s job to ensure all packets reach the target destination.
What is IPV4 protocol?
IPV4 (internet protocol 4) is an internet addressing system that is used to designate addresses to every device that wishes to connect to the internet. Every device that connects to the internet needs a serial number (IP address), IPV4 uses 32-bit addresses in five different classes, these are class: A, B, C, D, and E. Class D is used for multicasting, class E is reserved for future use, and classes A B C have a different bit length and these classes are used for addressing network hosts.
The maximum number of addresses IPV4 can allocate is 4.3 billion, considering every device needs to be allocated an address, IPV4 is fast approaching its limit and will not be sustainable for future allocation of addresses.
What is IPV6 protocol?
IPV6 (internet protocol 6) is an upgrade from IPV4.The basics of IPV6 are like IPV4 with the main improvement in IPV6 being that the IP addresses are lengthened from 32-bit address to 128-bit addresses. IPV6 also supports auto-configuration, which helps correct any shortcomings experienced when using IPV4.An example of this would be IPV4 does not allow credentials used to be forwarded to another host, IPV6 makes this possible and severs can use another sever to access another sever on behalf of the original sever.
Pros using IPV4
- Reliable security
When communication with other users it is important to encrypt the data, you are sending. There are now reliable security measures for IPV4 address packets that allows data to be encrypted.
- Large routing tasks
IPV4 network allocation is vital, it becomes easy to connect to multiple devices across a large network.
- Video libraries and conferences
Because of the large number of internet users, data transfer online ha become slow. IPV4 provides efficient data transfer and therefore provides a quality service for users.
- Flexible
Using IPV4 routing has become more scalable, this works well for large networks allowing data communication across networks to become more specific.
Cons using IPV4
While IPV4 is reliable and still widely used throughout the online world IP addresses are running out and is not sustainable in the long term.
- Internet use is expanding from browsing and searching data to users wishing to send more data in the form of video calls, video conferences, and online video libraries. IPV4 has limited functionality and over time has been adapted to facilitate the user’s needs.
Pros using IPV6
- Much larger address space
- Virtually unlimited host addresses
- Stateless auto configuration
- Automatic link local addressing
- Easy to type prefix lengths
- EUI 64 addressing
Cons using IPV6
- Privacy concerns
- Throttling bandwidth and banning users
- Tracking an individual personally
- Giving information to big business for lawsuits
- Giving information to the police for criminal actions
- Giving information to the government
- Using someone else’s connection to get them sued or arrested
- Difficulty with topology drawings
With all the extra space IPV6 provides it’s going to be a lot harder to fit prefixes on all of the topology drawings.
- System issues
Due to the length of the IP address IPV6 provides, in cases where you need to enter the IP address manually it may become troublesome for large networks or organisations.
References
https://www.lifewire.com/what-is-ipv4-ipv6-2483315 (IPV4)
https://www.techopedia.com/definition/5367/internet-protocol-version-4-ipv4 (IPV4)
http://benefitof.net/benefits-of-ipv4/ (IPV4 Pros)
http://ezinearticles.com/?IPv4-Vs-IPv6-(Advantages-and-Disadvantages)&id=5160096 (IPV4 Cons)
http://packetlife.net/blog/2010/apr/12/ipv6-pros-and-cons/ (IPV6 Pros)
http://ireport.cnn.com/docs/DOC-993739 (IPV6 cons)
https://greengarageblog.org/5-pros-and-cons-of-ipv6 (IPV6 cons)
https://www.howtogeek.com/175566/htg-explains-are-you-using-ipv6-yet-should-you-even-care/ (Support the change)
https://www.internetsociety.org/deploy360/ipv6/case-studies/ (cisco studies)
http://searchunifiedcommunications.techtarget.com/definition/Internet-Protocol (IP)
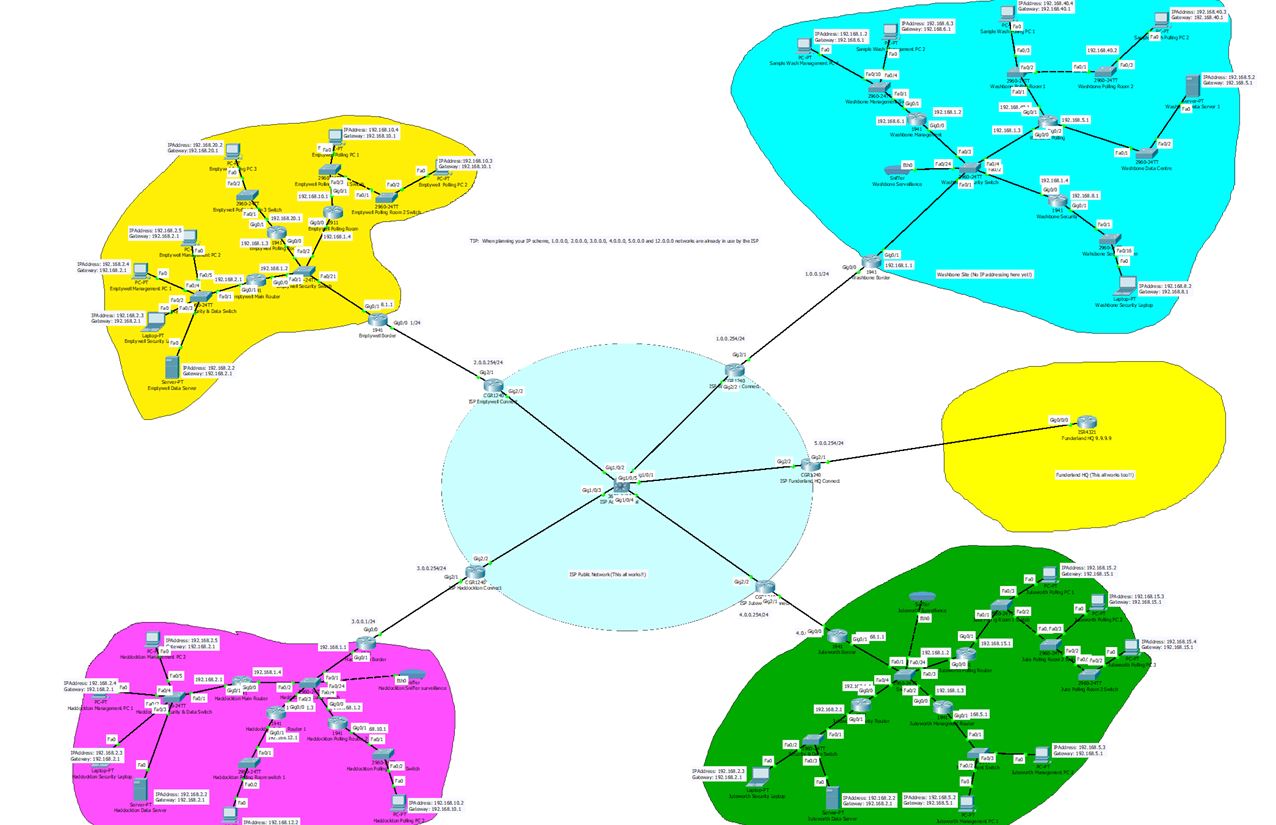
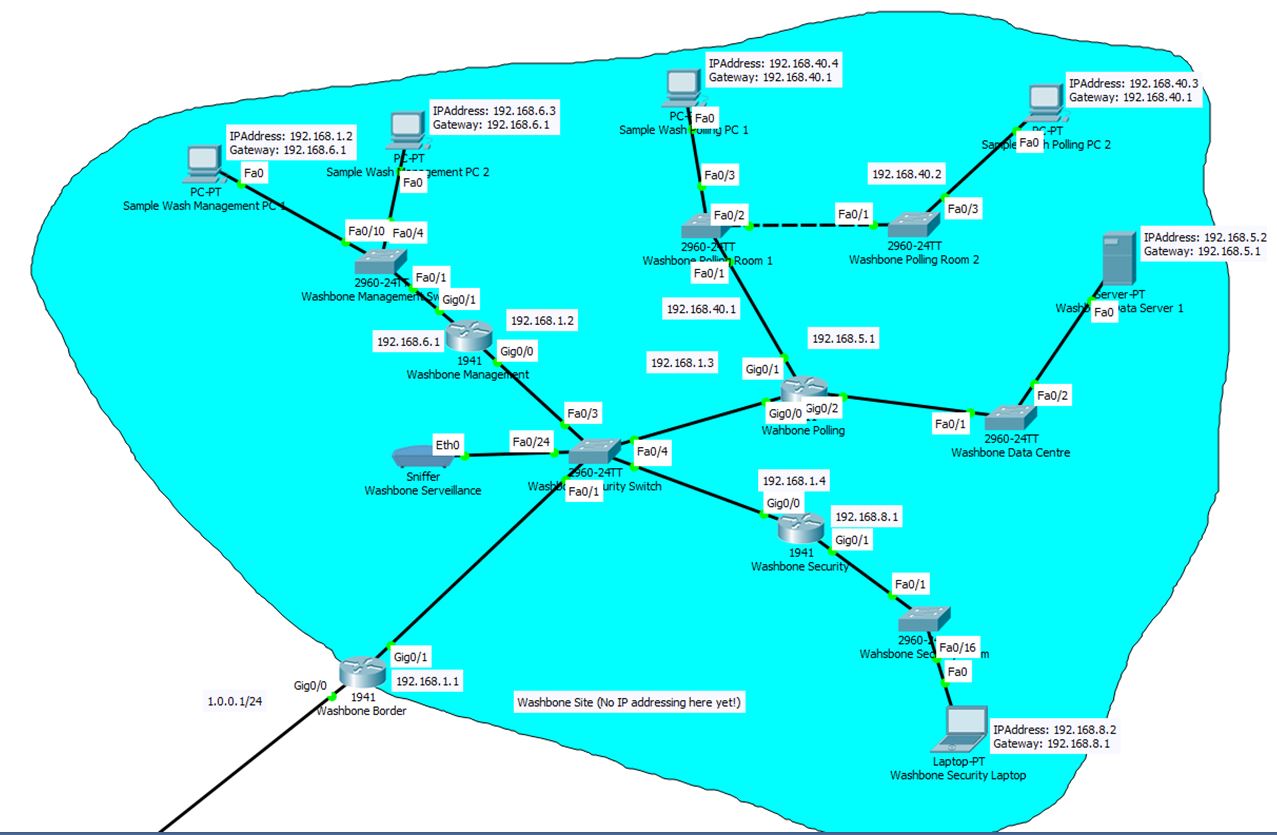
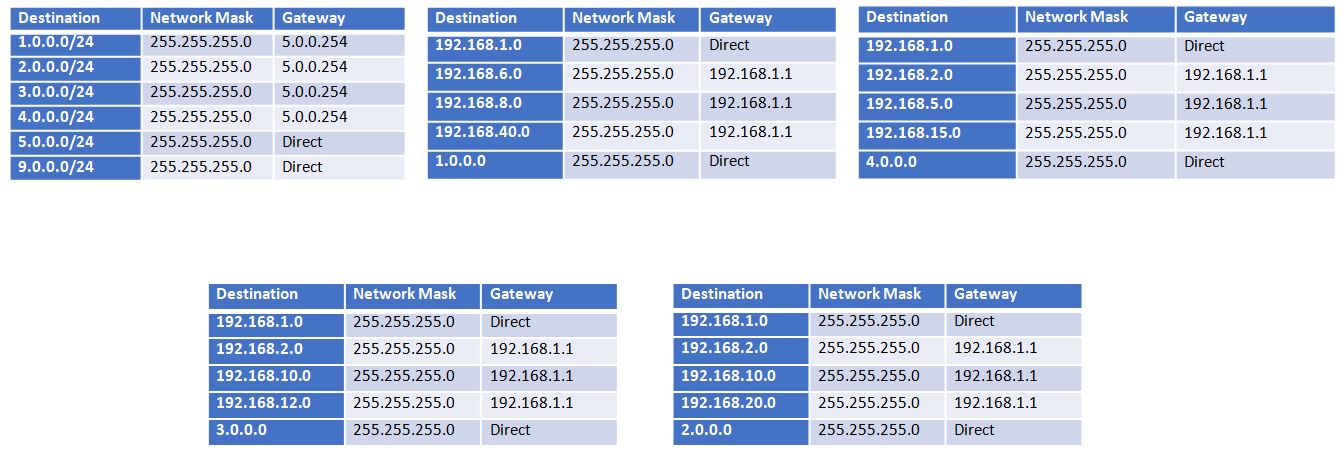
Security around polling stations
Cybercrime is on the increase and more recently outside influences are trying to manipulate local and general elections. Spire Network Design have gone to great measures to be able to confidently implement procedures that will ensure all the networks involved are secure and the public data is safely handled.
Spire Network Design Security Procedure outline:
- Networks
- Isolate networks that are involved in any part of the election.
- Keep documented record of all devices, its location, and its assigned owners.
- Ensure no device will have a default password including routers.
- Ensure all device passwords are strong and use many characters
- Backups
All critical data during elections will be frequently backed up and the backups will be stored on secure media not connected to the internet. All backups will not be overwritten, in the case a new copy of a backup is needed a new backup will be created. All backups that are created will be regularly tested to ensure that recovery is possible.
- Password and Permission Management
- Change default passwords and user names to ensure individual logins are available
- Restrict administrative access ensuring privileged users are closely monitored
- Voting System Preparation
- All devices used to transfer data will be brand new and not be reused once data is transferred.
- Once voting data is loaded into devices all the port on the device are sealed with tamper-evident seals.
- Tamper-evident seals will be numbered and logged, assigning the device serial number that the tamper-seal is related to.
- A Detailed record will be kept of all devices used before and during the election, this will ensure an accurate record of the devices.
- Transportation of the electoral results
All results will be transferred physically, this will be a pre-planned route and rehearsals regarding the transfer of data. Once the voting data is collected it would be written to disk then sealed once again with tamper-proof seal.
Spire Network Design are confident our security procedures will ensure a quick and secure transfer of data between networks. While security is our main priority, the speed and efficiency of the transfer of data is important as we believe security is improved the less time data is in transit.
Best practices ensuring polling data and voters privacy remains safe.
http://www.electoralcommission.org.uk/find-information-by-subject/electoral-fraud/electoral-fraud-vulnerabilities-review?a=155335 (electoral fraud)
https://www.electoralcommission.org.uk/__data/assets/pdf_file/0005/164255/EPE-Polling-station-handbook.pdf (polling station handbook)
https://aceproject.org/ace-en/topics/vo/vof/vof04/vof04d/default (security around polling stations)
https://www.ncsc.gov.uk/guidance/guidance-local-authorities-elections(gov guidance local)
https://www.ncsc.gov.uk/guidance/protecting-bulk-personal-data-main (protecting bulk data)
http://www.dos.pa.gov/VotingElections/OtherServicesEvents/Documents/DOS%20Guidance%20Electronic%20Voting%20System%20Security%2009232016.pdf (DRE polling network)
https://www.networkworld.com/article/3214388/lan-wan/how-to-plan-your-migration-to-ipv6.html (changing from ipv4 to ipv5)
https://www.smallnetbuilder.com/lanwan/lanwan-howto/32611-switch-your-network-to-ipv6 (Changing to ipv6)
Presentation Slides